Ever wondered how mstsc saves passwords? If you open an RDP file with a text editor like Notepad you can see the encrypted password. In this article I will show you how to encrypt and decrypt these passwords. Besides password recovery this enables you to create rpd files programmatically or perhaps update the password in many rdp files with a batch file.
So if we save a password with mstsc what does it look like? To see that open an rdp file with a text editor (eg Notepad) and you will see something like this:
screen mode id:i:1
desktopwidth:i:1280
desktopheight:i:750
session bpp:i:24
winposstr:s:2,3,188,8,1062,721
full address:s:MyServer
compression:i:1
keyboardhook:i:2
audiomode:i:0
redirectdrives:i:0
redirectprinters:i:0
redirectcomports:i:0
redirectsmartcards:i:0
displayconnectionbar:i:1
autoreconnection enabled:i:1
username:s:MyUserName
domain:s:MyDomain
alternate shell:s:
shell working directory:s:
password 51:b:01000000D08C9DDF0115D1118C7A00C04FC297EB0100000052A9E191EA75A948B359790578C9371A0000000008000000700073007700000003660000A8000000100000000A1DCCD2E50775CA25EC3857164B34DC0000000004800000A000000010000000FCE1A645B9B61AA450946BB6F955058108020000D83591CA47562D6DDAA689F050AE145039EBE22E00D1D3AEAA98373C7B63C3E8E7149072DF989EA43EFCE20513AD3D27B11BE7F17066A688E1DCE828AF85460AAC327B38E90776DB962888E4393D19637578984B19A187AAD95F6D2726ADE7DD315FF56C15FF5B3031014EDDCC3C24D1B81779AFDB006EE575F5BEFB8D2D2138D9D9D642BBB251CC5ED7226968764856EC660A646BACE748A13D6002A9A537AA70710615650B9387EED66DE28BD57B304BBDD7B581B943DA628EB0289E30A8BA784B76F7885BECCAB4FEF7820E97EE3C6E036EEAF6EAA669288DF2FCACC9BEC045C907EBBDE87AFB8CC6B07A600BD63AC891B61D95C2265DD9FD5E635D61BFBF5EDC28311375066611C610FB533D64515B643C82F57D9B183B05C156D91BC0974D38E546022B139E82452E6F1EDF76E52F732C3904E5E433F8F3D488DB0698427DBB0791A9F207F8CB6654CB8410BAF4A59C4F9E821E589ABC1E6E6E1D432181B690408F6884FE1007895A4D26D4A5A2C7458EE747DA35D44AC9FB08AB5477EA3E7CCDB3E37EE20FAFD0D0CF9584E420598B7003B347943AC28048F45E0FD21AD08148FFADCE0E7877219259A7BE722FFAE845A429BA2CF0A71F2D19EA7495530FABDB5106E8D404A38A7E6394C38457640EA7398C5D55F0C4D342CC6A39C77E10A2A5145AEA40B14F5C7C3760334D83C9BE748383FADE231248537353817D51F7B44F61B406ABC61400000071C354139F458B02D978015F785B97F7F6B307380
disable wallpaper:i:1
disable full window drag:i:1
disable menu anims:i:1
disable themes:i:0
disable cursor setting:i:0
bitmapcachepersistenable:i:1
As you can see the password is somehow encrypted before it was saved and automatically decrypted when you open the file with mstsc. .
I did some analysis on mstsc.exe and mstsc uses the functions CryptProtectData and CryptUnProtectData which are both exported by crypt32.dll. Since those API calls are documented let’s try to encrypt a password with mstsc and one ourselves and compare the output:
function CryptRDPPassword(sPassword: string): string;
var DataIn: DATA_BLOB;
DataOut: DATA_BLOB;
pwDescription: PWideChar;
PwdHash: string;
begin
PwdHash := '';
DataOut.cbData := 0;
DataOut.pbData := nil;
// RDP uses UniCode
DataIn.pbData := Pointer(WideString(sPassword));
DataIn.cbData := Length(sPassword) * SizeOf(WChar);
// RDP always sets description to psw
pwDescription := WideString('psw');
if CryptProtectData(@DataIn,
pwDescription,
nil,
nil,
nil,
CRYPTPROTECT_UI_FORBIDDEN, // Never show interface
@DataOut) then
begin
PwdHash := BlobDataToHexStr(DataOut.pbData, DataOut.cbData);
end;
Result := PwdHash;
// Cleanup
LocalFree(Cardinal(DataOut.pbData));
LocalFree(Cardinal(DataIn.pbData));
end;
So we encrypt the password “secret” and compare this with the same password saved by mstsc
MSTSC:
01000000D08C9DDF0115D1118C7A00C04FC297EB0100000052A9E191EA75A948B359790578C9371A0000000008000000700073007700000003660000A8000000100000000A1DCCD2E50775CA25EC3857164B34DC0000000004800000A000000010000000FCE1A645B9B61AA450946BB6F955058108020000D83591CA47562D6DDAA689F050AE145039EBE22E00D1D3AEAA98373C7B63C3E8E7149072DF989EA43EFCE20513AD3D27B11BE7F17066A688E1DCE828AF85460AAC327B38E90776DB962888E4393D19637578984B19A187AAD95F6D2726ADE7DD315FF56C15FF5B3031014EDDCC3C24D1B81779AFDB006EE575F5BEFB8D2D2138D9D9D642BBB251CC5ED7226968764856EC660A646BACE748A13D6002A9A537AA70710615650B9387EED66DE28BD57B304BBDD7B581B943DA628EB0289E30A8BA784B76F7885BECCAB4FEF7820E97EE3C6E036EEAF6EAA669288DF2FCACC9BEC045C907EBBDE87AFB8CC6B07A600BD63AC891B61D95C2265DD9FD5E635D61BFBF5EDC28311375066611C610FB533D64515B643C82F57D9B183B05C156D91BC0974D38E546022B139E82452E6F1EDF76E52F732C3904E5E433F8F3D488DB0698427DBB0791A9F207F8CB6654CB8410BAF4A59C4F9E821E589ABC1E6E6E1D432181B690408F6884FE1007895A4D26D4A5A2C7458EE747DA35D44AC9FB08AB5477EA3E7CCDB3E37EE20FAFD0D0CF9584E420598B7003B347943AC28048F45E0FD21AD08148FFADCE0E7877219259A7BE722FFAE845A429BA2CF0A71F2D19EA7495530FABDB5106E8D404A38A7E6394C38457640EA7398C5D55F0C4D342CC6A39C77E10A2A5145AEA40B14F5C7C3760334D83C9BE748383FADE231248537353817D51F7B44F61B406ABC61400000071C354139F458B02D978015F785B97F7F6B307380
CryptRDPPassword:
01000000D08C9DDF0115D1118C7A00C04FC297EB0100000052A9E191EA75A948B359790578C9371A0000000008000000700073007700000003660000A800000010000000F68F88DF66E436846C077BF402E46EB90000000004800000A000000010000000FE8CEBCF943F9CEC9F3C3A1E0710BEC510000000A647D6ADB728E51F071C854F0BFFF66F140000003B271D41D3D256BCCC4DD255701C14B7489A081D
As you can see the length of a password encrypted by mstsc is 1329 bytes and the one from CryptRDPPassword is smaller. Actually mstsc generates fixed length passwords and our function’s length is based upon the password. Even more strange is that mstsc password is always 1329 bytes because the input password is unicode which should produce an even size length. It doesn’t really matter though because mstsc.exe accepts the smaller sized passwords without any problems.
For now I will leave with a demo tool I wrote to encrypt and decrypt rdp passwords. But in a followup article I will show you how te encrypt the passwords to the full length 1329 bytes the same way mstsc does.
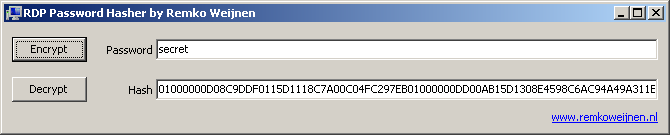
Remote Desktop Password Encryption & Decryption Tool
Do you find this article usefull, why not leave a comment?
原文:https://www.remkoweijnen.nl/blog/2007/10/18/how-rdp-passwords-are-encrypted